OpenID Connect
Note: If you plan to use OpenID Connect as your authentication method you'll need to start by creating the application in Auth0 that will be used to authenticate your users. Please see the Setting Up Okta Powered by Auth0 topic first to create and setup your Auth0 application before continuing with the steps below.
Setting Up Application Manager (TDS) to use Auth0/Okta with OpenID Connect for Authentication For the First Time:
Before proceeding, you need to ensure that the Admin role is set as the default New user's role.
- Open Application Manager and navigate to Administration > Security Settings >Access and Roles and confirm Admin Users is selected.
- Next set up your Roles, Role Privileges and User Claims as preferred. Once those are set up proceed to step 3.
- Navigate to Administration > Authentication and select OpenID Connect.
- Enter the Issuer, Client ID, and User Info Client URI noted while setting up the AuthO application.
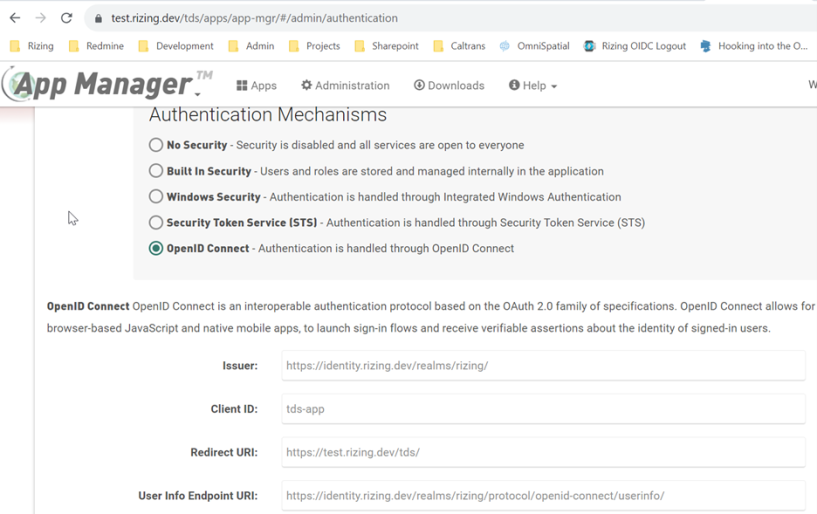
- Use your Application Manager (TDS) base URL as the Redirect URI.
- Click Save and then click Change to confirm your changes.
- The application will now restart. Lastly, you need to update the default role back to a standard user role.
- Navigate to Administration > Security Settings > Access and Roles and select Standard Users (or your organization's equivalent) as the New user's default role.
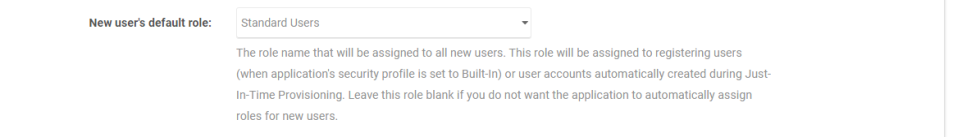
- Click Save.
